A common taxonomy aligns cybersecurity definitions and terminologies to enable the categorisation of existing institutions and expertise across Europe. This categorisation is crucial to facilitate the potential collaboration among these institutions and consequently to foster the establishment of the Competence Centre and Network.
The taxonomy created by the European Commission Joint Research Centre (JRC) is based on a comprehensive set of standards, regulations and best practices, and it has been validated by different EU cybersecurity stakeholders, such as the European Cyber Security Organization (ECSO). It was further enhanced based on feedback provided by the four cybersecurity research and competence network pilot projects (CONCORDIA, ECHO, SPARTA and CyberSec4Europe), which embrace over 160 partners including companies, SMEs, universities and research institutes.
A similar knowledgebase, if integrated with other existing databases (e.g., patents, European projects, research production, scientific profiles), will be also extremely relevant in the assessment of the R&D cybersecurity position of Europe. This would provide useful information to identify weaknesses and where and how to act to reach a homogeneous development of the cybersecurity domain.
The JRC Cybersecurity Taxonomy is built on four dimensions, namely Knowledge domains (or simply Domains, each of them with a set of subdomains), Sectors, Technologies, Use cases (see picture below). More information about the taxonomy and the related EU Vocabulary can be found at the following URLs:
- https://publications.jrc.ec.europa.eu/repository/handle/JRC125533
- https://data.jrc.ec.europa.eu/dataset/d2f56334-a0df-485b-8dc8-2c0039d31122
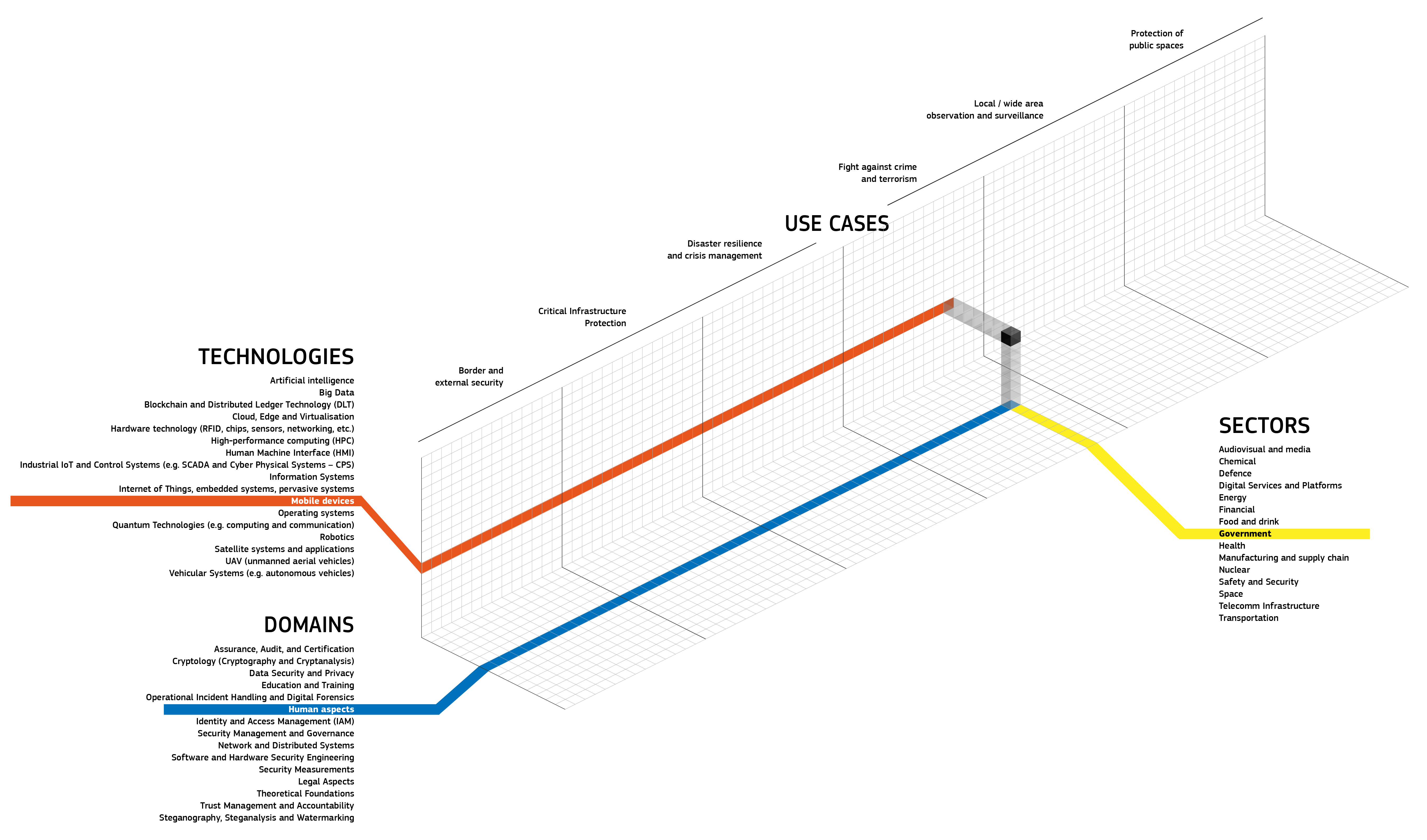
The image above shows the elements of the four dimensions of the JRC Cybersecurity Taxonomy.
